Microsoft Sentinel SIEM allows businesses to centralize analyse and investigate security incidents. IPs are a common entity variable within these security incidents. Investigating the Threat Intelligence (TI) reputation of every single IP manually is a significant drain on SOC analyst time. What if we could automate this first step with SOAR (Security Orchestration Automation and Response), enriching Sentinel (XDR) security incidents with valuable threat intelligence almost instantly. This blog post elaborates on how to achieve this with the AbuseIPDB API together with the help of an Azure Logic App.
AbuseIPDB - balancing costs and capabilities
Many security engineers initially think of VirusTotal (VT) for automated IP and domain name threat intelligence lookups. VirusTotal has recently been acquired by Google Threat Intelligence, which incorporates Mandiant intelligence. VirusTotal is arguably one of the most recognized names in the space, offering comprehensive TI lookups for IPs, domains, and file hashes. However, using the VirusTotal API comes at a significant cost nowadays. While a free VirusTotal API exists, it is only for non-commercial use and has rather tight rate limits of only 500 API lookups per day, which is rather limited. The commercial VirusTotal API license and platform starts at around $75K USD per year (Q1 2025).
Microsoft provides an integratable alternative to VirusTotal’s new Google Threat Intelligence platform called Microsoft Defender Threat Intelligence (MDTI). The free tier of MDTI offers limited Threat Intelligence feeds. While the premium version of MDTI offers incident enrichment for approximately 43K USD per year (Q1 2025). Both can be a costly investment for most businesses.
AbuseIPDB specializes in IP reputations, both for IPv4 and IPv6, and crowd-sourcing reports of malicious activity. To automatically enrich IP addresses in Sentinel incidents with AbuseIPDB reputation scores and details, enabling fast SOC analysing and prioritization for response, using a cost-effective solution for showing the likelihood of an IP being malicious along with details like usage type, ISP, country, and total malicious reports. Domain lookups with AbuseIPDB are limited, and file hash lookups are not available with AbuseIPDB. The free API of AbuseIPDB is only for non-commercial use and has a rate of 1.000 lookups per day. The paid version of AbuseIPDB starts at only $228 USD per year with a rate limit of 10.000 lookups per day (Q1 2025). This API rate limit automatically resets after 24 hours when violating the threshold, meaning the Logic App for SOAR incident enrichment would simply start processing new Sentinel incidents.
Building the AbuseIPDB Logic App
The AbuseIPDB Logic App from the Azure Marketplace did not work for us as desired. This is why we have crafted a new consumption based Logic App below:
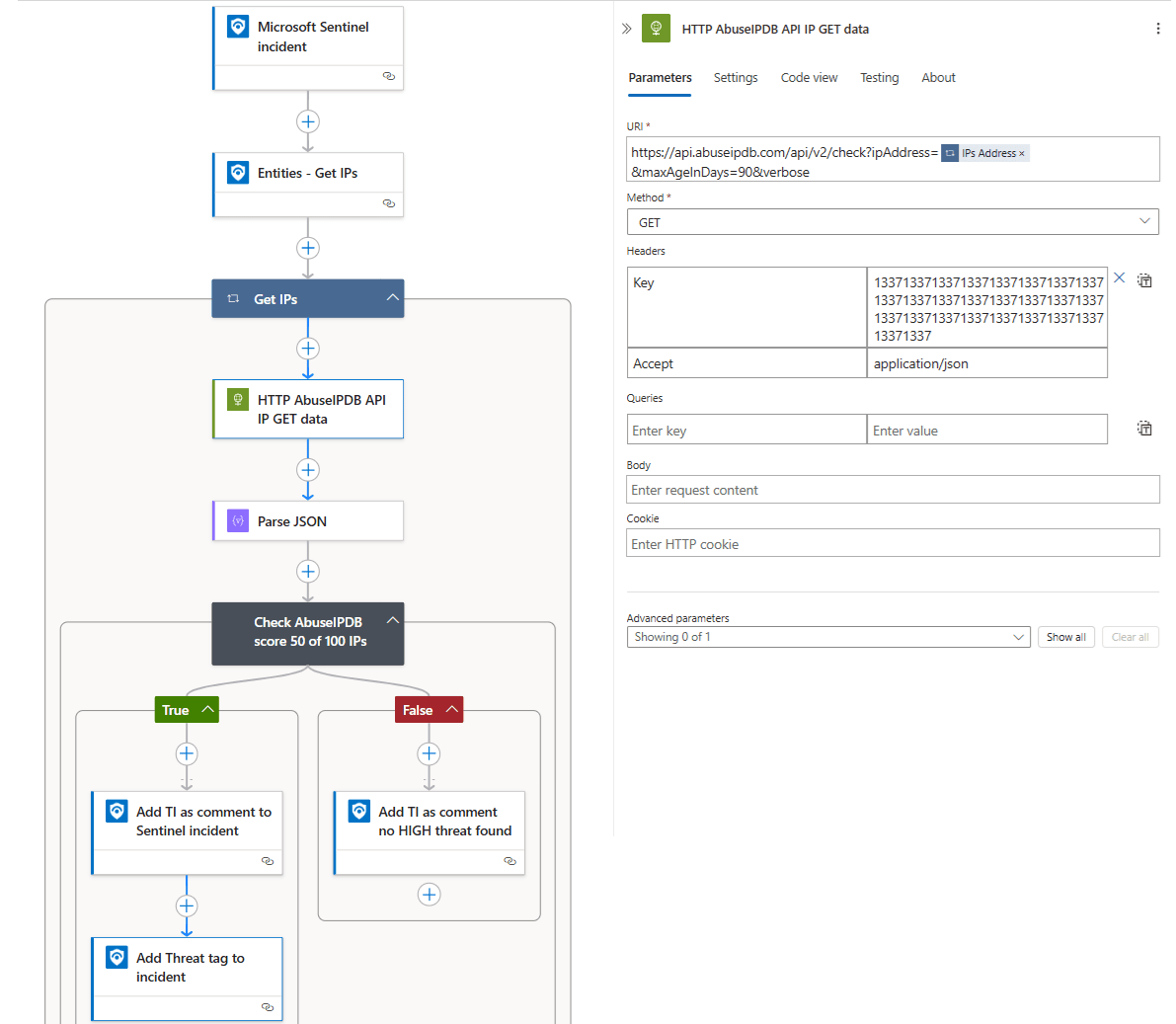
Figure 1: AbuseIPDB Logic App design
Step 1: Trigger from Sentinel Incident
This Logic App starts with the Microsoft Sentinel incident trigger. This means the Logic App, referred to as a Sentinel Playbook, is designed to be attached to an incident, which you can later configure with a Sentinel Automation Rule.
Step 2: Get IPs from the Sentinel Incident
Sentinel incidents contain structured and parsed data, including identified entities such as IP addresses, accounts, and hosts. We need to specifically grab the IPs using The Logic App action Entities - Get IPs (Preview) Sentinel connector action. The Entities List field is populated with the Entities dynamic content from the Sentinel Incident Trigger. This action filters and extracts just the IP address entities from the incident's full entity list. Entities list: Entities.
Step 3: Loop Through Each IP Address
An incident might involve multiple IP addresses. Therefore, we need to process each one individually. The Logic App action: For each control loop, named Get IPs. Configuration: The select output is set to IPs dynamic content, which is the output list of IP addresses from the previous step. Make sure under Settings, Concurrency control is configured to '1'. This loop will execute the contained actions once for every IP address found. Unfortunately, Logic Apps do not have a built-in function to perform a sanity check if an IPv4 or IPv6 address is either Public or Private. Therefore, you need to create an extra custom Condition action to check if the Entity IP address starts with 10. and 192.168. and 172.16 and 172.0 and ::1 and fe80 and fd00. This could potentially save AbuseIPDB API calls because looking up TI on private IPs is rather pointless.
Step 4: Query AbuseIPDB API
Inside the loop, for the current IP address being processed, we call the AbuseIPDB API using the Logic App action: HTTP built-in connector. By using the method GET for URI: https://api.abuseipdb.com/api/v2/check?ipAddress= followed by the dynamic content IPs Address, which represents the current IP address from the loop. We use the query parameters &maxAgeInDays=90&verbose. Verbose provides more detailed results and maxAgeInDays=90 limits results to reports in the last 90 days. In the header, specify the AbuseIPDB API key with Key. Note: use Azure Key Vault to store your AbuseIPDB API key. Never hardcode API keys directly in the Logic App.
Step 5: Parse the AbuseIPDB API Response
Next, the AbuseIPDB API returns TI data in JSON format. To easily use specific fields, like the AbuseIPDB confidence score, we need to parse the JSON data. We use the Logic App action: Parse JSON. Set to the Body dynamic content from the HTTP API data from the previous action. The AbuseIPDB JSON schema can be found here.
Step 6: Check AbuseIPDB data
Now we can evaluate the IP AbuseIPDB TI results. We do this by defining the Logic App action: Condition. This condition checks if the abuseConfidenceScore from the Parsed JSON is greater or equal to 50. You can adjust this scoring threshold based on your organization's risk tolerance. We add logic app action: Add comment to incident (V3) by defining the incident ARM ID using the Incident ARM ID dynamic content from the Sentinel Incident trigger. The incident Comment Message includes:
- The analyzed IP address (ipAddress from Parse JSON).
- The AbuseIPDB Confidence Score (abuseConfidenceScore from Parse JSON).
- Total Reports (totalReports from Parse JSON).
- Unique Users Reporting (numDistinctUsers from Parse JSON).
- Last Reported Date (lastReportedAt - needs a formatDateTime function when it is null).
- ISP (ISP variable from Parse JSON).
- Country (countryName from Parse JSON).
- Comments (detailed source of the Threat Intelligence data from Parse JSON).
Step 7: Add Sentinel Threat tag
Lastly, we add a Threat tag to the Sentinel incident using the Update incident Logic App action. If the AbuseIPDB score is less than 50 out of 100, we can state in the incident comments the analysed IP address is not a high risk according to AbuseIPDB Threat Intelligence.
SOAR
While you can run this Logic App manually from a Sentinel incident, the real power comes with SOAR automation. By using Sentinel Automation, we can run the Logic App as a Playbook for each Sentinel security incident triggered by an Analytics Rule. Also have a look at the AlienVault OTX API, which can be used commerically without costs and uses different Threat Intelligence sources. AlienVault can also analyse domain names in more depth, and file hashes. You can run mulitple Sentinel Playbook's for a single Sentinel Incident, therefore quering different Threat Intelligence sources.
We can also extend the Logic App by adding the IP address to the Defender XDR blocklist, effectively blocking network connectivity. In buzzword terms, achieving SOAR. Read this article for more info.
There are many other use-cases and alerts which can be created based on your environment and business risks. Are you missing important alerts? Is your SIEM outdated? Contact us if you want to take your SIEM to the next level.





