Cisco Meraki Wireless (MR), Switches (MS), and Firewall (MX) appliances integrate the open-source based SNORT Intrusion Detection and Prevention System (IDPS). The Cisco Meraki SNORT engine uses IDPS signatures maintained by the SNORT community and the Cisco Talos Threat Intelligence team.
Cisco Meraki Security Configuration
You can configure your Cisco Meraki in Prevention mode (IPS) or Detection mode (IDS). In order to prevent business impact, start with the "Balanced" IDPS baseline and change the Cisco Meraki IDPS configuration to the "Security" baseline after filtering non-malicious SNORT signatures based on source, destination and signature ID. In case the IDPS Signature title does not give enough information, you can search based on Signature ID for more details.
The "Security" baseline contains IDPS signatures that are from the current year and the previous three years for vulnerabilities with a CVSS score of eight (8) or greater and are in one of the categories: Malware-CNC (Command and Control), Blacklist (IP's, DNS names, URL's and user-agents), SQL injection, Exploit kit, App-detect (unwanted or possible malicious applications).
Cisco Meraki Advanced Malware Protection (AMP) is a malware detection module. If a system behind a Cisco Meraki MX appliance downloads a file, the file hash is checked against Cisco's database of known malicious hashes of files, similar to VirusTotal. If the hash of a file is unknown (first seen), a behavioural file analysis executed by Cisco Threat Grid. Note: files over 5MB are not inspected. Furthermore, not all files under 5MB are inspected, only PE executables, Zip files, DLLs, PDFs and Office documents.
Cisco Meraki appliances can also apply content filtering to block possible malicious categories of web traffic based on your organizational policies. From a security perspective, it is rather essential to block network activity marked as threats. You can block the following network categories: Malware Sites, Spyware and Adware, Phishing, Spam, Exploits, Mobile Threats, High-Risk Sites and Locations, Bogon, P2P Malware Node, Ebanking Fraud, Indicators of Compromise (IoC), Domain Generated Algorithm, Open HTTP Proxy, Open Mail Relay, TOR exit Nodes, Potential DNS Rebinding, DNS Tunneling, Dynamic DNS, Newly Seen Domain, Cryptojacking, Linkshare, Malicious Sites and Botnets.
After configuring your Cisco Meraki, it is time to forward the Cisco Meraki security logging to Sentinel SIEM. Forward your Cisco Meraki security logging indirectly via a (Linux-based) rsyslog logging server, running the Sentinel AMA-agent (recommended) or the OMS-agent. Meraki security alerts are collected with the Log type "security_event" category. This means you can either 1) forward all network traffic if you want Sentinel SIEM Threat Intelligence applied on all network streams or 2) rely on Cisco Meraki proprietary detection methods and only process the "security_event" log items. Forwarding network logging can be costly, depending on your baseline network traffic. Sentinel SIEM ingestion costs are approximately 2x$2.46 dollar per GB as of this date. We advise you first to conduct a Sentinel Cisco Meraki costs analysis or use the costs preview feature in Sentinel. The latter can save you significant Sentinel SIEM ingestion costs. Also check your Cisco license which security modules are included. Next, you can use our Cryptsus tuned Meraki_CL KQL function parser to map raw Syslog logging to Sentinel variables. Follow the Microsoft Sentinel log parser configuration steps. The log forwarding flow is shown in Figure 1:
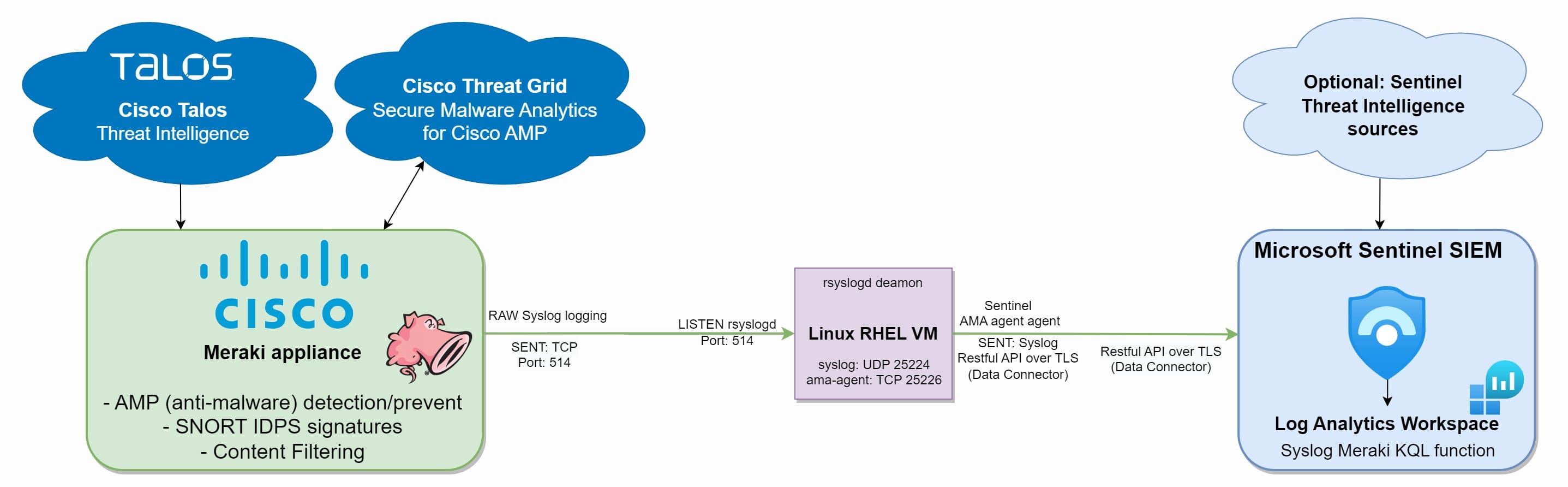
Figure 1: Cisco Meraki connecting to Sentinel SIEM Workspace
This blog post shares 8 Cryptsus Cisco Meraki Firewall SOC threat hunting use-cases for possible suspicious network activity, including IoA's and IoC's. Most of the below use-cases are crafted by thinking like a malicious actor. We also consider the MITRE ATT&CK framework into account to mirror the different Sentinel use-cases against known attack phases to craft your own KQL (Kusto Query Language) use-cases.
1. Cisco Meraki IDPS and malware alert from WAN to LAN
//cryptsus.com - we craft cyber security solutions
//Cisco Meraki IDS is Snort based. Use https://www.snort.org/rule_docs/ to lookup more details about the IDPS signature. Example: can lookup the IDPS signature by re-writing it: 1:45549:4 -> search for: 45549
let GeoIPDB = _GetWatchlist("GeoIPDB");
CiscoMeraki
| where LogType == "security_event"
| where ipv4_is_private(SrcIpAddr) == false
| where Message !contains_cs "attempt"
| evaluate ipv4_lookup(GeoIPDB, SrcIpAddr, network, return_unmatched = true)
| project TimeGenerated, DeviceName, EventSeverity, Message, Action, SrcIpAddr, country_name, SrcPortNumber, DstIpAddr, DstPortNumber, Signature
| sort by TimeGenerated2. Cisco Meraki IDPS and malware attack from LAN to WAN
//cryptsus.com - we craft cyber security solutions
//Cisco Meraki IDS is Snort based. Use https://www.snort.org/rule_docs/ to lookup more details about the signature. You can lookup the signature by re-writing it: 1:21516:9 -> Search for: 21516
CiscoMeraki
| where LogType == "security_event"
| where ipv4_is_private(SrcIpAddr)
| where Message !contains_cs "attempt"
| summarize count() by DeviceName, EventSeverity, Message, Action, SrcIpAddr, DstIpAddr, DstPortNumber, Signature
3. Cisco Meraki IP match with Sentinel Threat Intelligence sources. Note: configure your Sentinel Threat Intelligence sources first.
//cryptsus.com - we craft cyber security solutions
CiscoMeraki
| where LogType == "security_event"
| distinct SrcIpAddr
| project SrcIpAddr
| join kind = inner (
ThreatIntelligenceIndicator
| where NetworkIP != ''
) on $left.SrcIpAddr == $right.NetworkIP4. Cisco Meraki LAN IP match with Sentinel Threat Intelligence sources
//cryptsus.com - we craft cyber security solutions
CiscoMeraki
| where LogType == "security_event"
| distinct DstIpAddr
| project DstIpAddr
| join kind = inner (
ThreatIntelligenceIndicator
| where NetworkIP != ''
) on $left.DstIpAddr == $right.NetworkIP5. Cisco Meraki LAN DNS match with Sentinel Threat Intelligence sources
//cryptsus.com - we craft cyber security solutions
CiscoMeraki
| distinct Url
| project Url
| extend Host = tostring(parse_url(Url).Host)
| join kind = inner (
ThreatIntelligenceIndicator
| where DomainName != ''
) on $left.Host == $right.DomainName6. Cisco Meraki possible malicous HTTP requests
//cryptsus.com - we craft cyber security solutions
CiscoMeraki
| where isnotempty(HttpRequestMethod)
| where HttpRequestMethod == "PUT" or HttpRequestMethod == "DELETE" or HttpRequestMethod == "POST"
//Whitelist legitimate HTTP requests
| where Url !startswith_cs "http://update.googleapis.com/"
| distinct Url, HttpRequestMethod7. Cisco Meraki detecting connection to possible malicious port
//cryptsus.com - we craft cyber security solutions
let VerySuspiciousPorts = (_GetWatchlist('suspiciousports') | project dest_port);
//Source: https://github.com/mthcht/awesome-lists/blob/main/Lists/suspicious_ports_list.csv
CiscoMeraki
| where DstPortNumber in (VerySuspiciousPorts)
| project TimeGenerated, SrcIpAddr, DstIpAddr, SrcPortNumber, DstPortNumber, HttpRequestMethod, Url, SrcMacAddr, NetworkProtocol
//Exclusion list
| where DstPortNumber != "8443" and DstPortNumber != "8080"
| where Url !startswith_cs "https://speed.cloudflare.com"
| sort by Url8. Cisco Meraki portscan detected
//cryptsus.com - we craft cyber security solutions
let PortScannedTotal = 50;
CiscoMeraki
| where NetworkProtocol == "UDP" //change to TCP to detect TCP port scans
| where SrcIpAddr != "127.0.0.1" and SrcIpAddr != "::1"
| summarize PortsScanned=dcount(DstPortNumber), ConnectedPorts=make_set(DstPortNumber, 100) by SrcIpAddr, bin(TimeGenerated, 6m)
| where PortsScanned > PortScannedTotal
//Possibly whitelist of vulnerability scanner IP's:
//| where SrcIpAddr == ""There are many other use-cases and alerts which can be created based on your environment and business risks. Are you missing important alerts? Is your SIEM outdated? Contact us if you want to take your SIEM to the next level.





